Just some tips of the day. It is not a step-by-step guide.
Office Web Apps Side
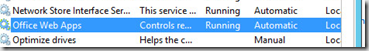
1. Office Web Apps must be installed ![]()
Use the script below to simplify prerequisites installation
Add-WindowsFeature Web-Server,Web-Mgmt-Tools,Web-Mgmt-Console,Web-WebServer,Web-Common-Http,Web-Default-Doc,Web-Static-Content,Web-Performance,Web-Stat-Compression,Web-Dyn-Compression,Web-Security,Web-Filtering,Web-Windows-Auth,Web-App-Dev,Web-Net-Ext45,Web-Asp-Net45,Web-ISAPI-Ext,Web-ISAPI-Filter,Web-Includes,InkandHandwritingServices
2. You have to request and assign certificate for OWA services
Add machine to domain, request new certificate (CN=internal FQDN) and create new Office Web Farm with defined external and internal URLs
How to request certificate? IIS Manager –> Server Name > Server Certificates and select “Create Certificate Request” from Actions pane, fill in all the form fields and save your request in the txt format.
To issue certificate, you can use your internal CA and CA Web Services (just go to http://<ca_fqdn>/certsrv) and past your request to the web box , select Web Server template and download certificate
To import, go to the Server Certificates in IIS and click on “Import..” or use Certificates snap-in for local machine account. Required certificate must be located under Certificates –> Personal
Check site bindings and select SSL certificate (created on the previous step)
3. You must have a configured Office Web Apps Farm
To create new farm use New-OfficeWebAppsFarm cmdlet:
New-OfficeWebAppsFarm -ExternalURL “https://<external>.domain.com” -InternalURL “https://<internal>.domain.com” -CertificateName “Friendly Name Of Certificate”
Check status of “Office Web Apps” Service (sometimes it goes to Stopped and you cannot start service. one of the reasons is invalid certificate)
Open IE and past “https://<owa_internal_FQDN>/hosting/discovery .

If you got the above response, check the 4th requirement
4. Office Web Apps should be defined in Skype For Business topology and discovered by Front-End
Open Skype Topology Builder and update it with Office Web Apps Internal URL (add Office Web Apps Server + associate it with your pool), publish topology then
Web Conferencing Server discovers Office Web Apps Server automatically after enabling updated topology.
Check event logs and find information record from LS Data MCU (some minutes are required for discovery. don’t panic)
5. DNS records (DNS A record for internal should be existed, DNS A record for external URL must be created manually)
IIS/ARR Side
1. IIS 8.0 and IIS ARR 3.0 are recommended components for “free” reverse proxy solution (IIS goes with the default settings, ARR 3.0 installed using Web Platform Installer). TMG and UAG are discontinued.
2. Reverse Proxy should have at least 2 NICs (DMZ, External). DMZ without any gateways and DNS servers. Use static route to the network, where FE/OWA are deployed and hosts file for DNS resolution.
It is possible to deploy DNS and other servers in DMZ but it’s quite unnecessary.
If Reverse Proxy is located behind NAT – at least 1 NIC is required (DMZ) . Source and Destination ports for DNAT: TCP 80 and 443
Example of hosts file:
10.2.3.20 fe01.contoso.com
10.2.3.21 fe02.contoso.com
10.2.3.24 owa.contoso.com <office web apps server>
3. Reverse proxy must have DNS suffix
4. As a best practice, you need to request 2 public certificates (1 for Edge Services <not covered here> and 1 for Reverse Proxy). Wildcard is supported only for SAN entries
Option 1:
SN=extweb.company.com <external Web Services FQDN>
SAN=lyncdiscover.company.com
SAN=meet.company.com <simple URL for meet>
SAN=dialin.company.com <simple URL for dialin>
SAN=owaext.company.com <Office Web Apps External URL>
Option 2:
You can reduce cost of certificate by using simple URLs based on the 1 domain name skype.company.com (skype.company.com/meet and etc).
Therefore,you need only one external DNS A record + 1 SAN entry in a certificate which enables all three types of simple URLs.
SN=extweb.company.com <external Web Services FQDN>
SAN=lyncdiscover.company.com
SAN=skype.company.com <simple URLs>
SAN=owaext.company.com <Office Web Apps External URL>
Option 3:
Wildcard as a SAN entry
SN=extweb.company.com <external Web Services FQDN>
SAN=*.company.com <Wildcard that covers simple URLs and lyncdiscover>
Option 4:
Officially unsupported. Wildcard as a Subject Name.
Note: Works for edge services as well . I’ve tested the basic functionality (except external federation)
SN=*.company.com
SAN=*.company.com
SAN=company.com
5. Assign public certificate to reverse proxy
MMC > add snap-in “Certificates> for local machine and import certificate to Personal
or use IIS –> Server Certificates –> Import on the right pane
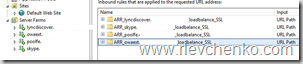
6. ARR should have server farm and URL Rewrite Rules associated with Office Web Apps
Farm Properties: disk caching and ssl offloading disabled, proxy time-out 200
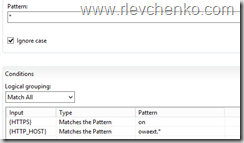
IIS –> server name –> URL Rewrite and check or add rule for Office Web Apps.
For security reasons it’s recommended to allow only https (Condition input:HTTPS and pattern ON). If rule does not have condition for HTTPS , rule accepts both HTTP and HTTPS requests.
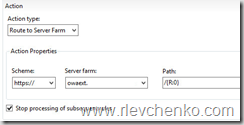
Action Type for all rewrite rules should be: route to server farm
Using: Wildcards
Note: for simple urls, external web services, lyncdiscover you can use the same procedure of creating farm and rewrite rules with one exception: Front-end listens 8080 and 4443 ports so you have to change default 80 and 443 ports to the required if you are adding rules for external Skype Web Services. For OWA we don’t need to change default settings
If https://<owa external url>/hosting/discovery does not work..
1) check rewrite urls (someone uses regular expressions and it’s very easy to make mistake while defining rewrite conditions)
2) verify farm members status under <server farm name>-“Monitoring and Management”
3) 443 port should be opened and accessible from external networks (xml file may be downloaded from internal and external sides as well). If you created Office Web Apps with AllowHTTP parameter, you need to check 80 port as well
4) check SFB topology (do not forget to download current topology version before verification) and event logs on FE
5) check Office Web Apps service status
7. Firewalls between reverse proxy, front-end and office web apps + edge firewalls should be configured.
8. Create new online meeting, attach PowerPoint presentation and enjoy ![]()
Useful links: